Metasploit
Metasploit is a framework created to provide information about security vulnerabilities, and aid in penetration testing. It consists of four main libraries:
- Exploits (e.g. root privilege escalation)
- Auxiliaries – or exploits without payload (e.g. scanners, fuzzers)
- Payloads - code that runs remotely (e.g. reverse TCP shell or Bind TCP shell)
- Encoders
These four will allow you to use the frameworks 1677+ exploits to test or attack a system.
The framework can be opened by clicking on the tiles seen on the picture bellow, and searching for it by starting to type Metasploit and the clicking the icon.

Another method is simply navigating to the terminal and type:
msfconsole
Either way you will get at picture like the one bellow
It might be another drawing than the cow ;P
Now you can continue on following this guide which contains two examples on security vulnerabilities that can be exploited with Metasploit.
Heartbleed
The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web and email.
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software.
The goal is to find a host that is running an vulnerable version of OpenSSL, this can be done by using Nmap and the script bellow.
nmap -p 443 IP-address/24
When you have identified a possible target try searching in Metasploit for possible exploits.
Vulnerability exploitation
Outdated systems is often an easy target due to Public vulnerabilities. In this case you will need to use what you know about fingerprinting to find information about the hosts in the network. One method of doing this is using the Nmap to give information about the operating system by using the command bellow.
nmap -O IP-address/24
This will provide you with a picture like the one below.
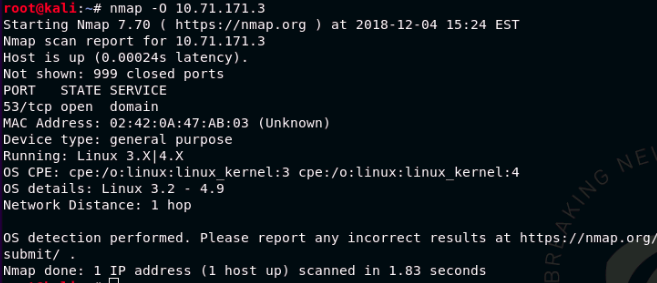
This gives you the information about which services that is running on each device. In this case the host in running some version of Linux.
The goal is now to find an outdated operating system that might be vulnerable. And find exactly which service package it is, and then search google for possible exploit that exist in the Metasploit framework.