Network sniffing
Everything you do online is transmitted through countless routers and switches on the way to the final destination. Basically all these packets are susceptible to collection and analysis at each of those points, this is done by a process called packet sniffing.
The most common way of networking is Transmission Control Protocol over Internet Protocol (TCP/IP), which means that the network sends TCP-packets to the final host using IP-addresses.
What you should note is that the data is send in packets, this means that when you send an e-mail it is not send as the complete e-mail it is disassembled into smaller data packets, and then assembled at the receiving host. As these smaller data packets are travelling across the Internet they are not only susceptible to collection but even modification.
To get an more in depth understanding about sending data via. TCP/IP. We recommend that you take a quick look at the wikipedia article about TCP/IP stack.
Wireshark
One of the many tools that can be used for packet sniffing and analysis is a program called Wireshark.
Starting Wireshark
There is two options for starting Wireshark, you can open it by navigating to the terminal and type:
wireshark
Or you can open or you can open it by clicking at the tiles seen on the picture bellow, and searching for Wireshark by starting to type Wireshark and then clicking the icon of a shark fin.

When the program is started, press ok to the pop-up.
Now you are met by the screen bellow, this is the networks that you can chose to listen to, since we want to listen to the network our computer is in, we pick eth0 by double clicking it.
Now we can see all the packets send in the network, the next part is analysing them.
Reading packets
You will be meet by a screen like the picture bellow after clicking on eth0
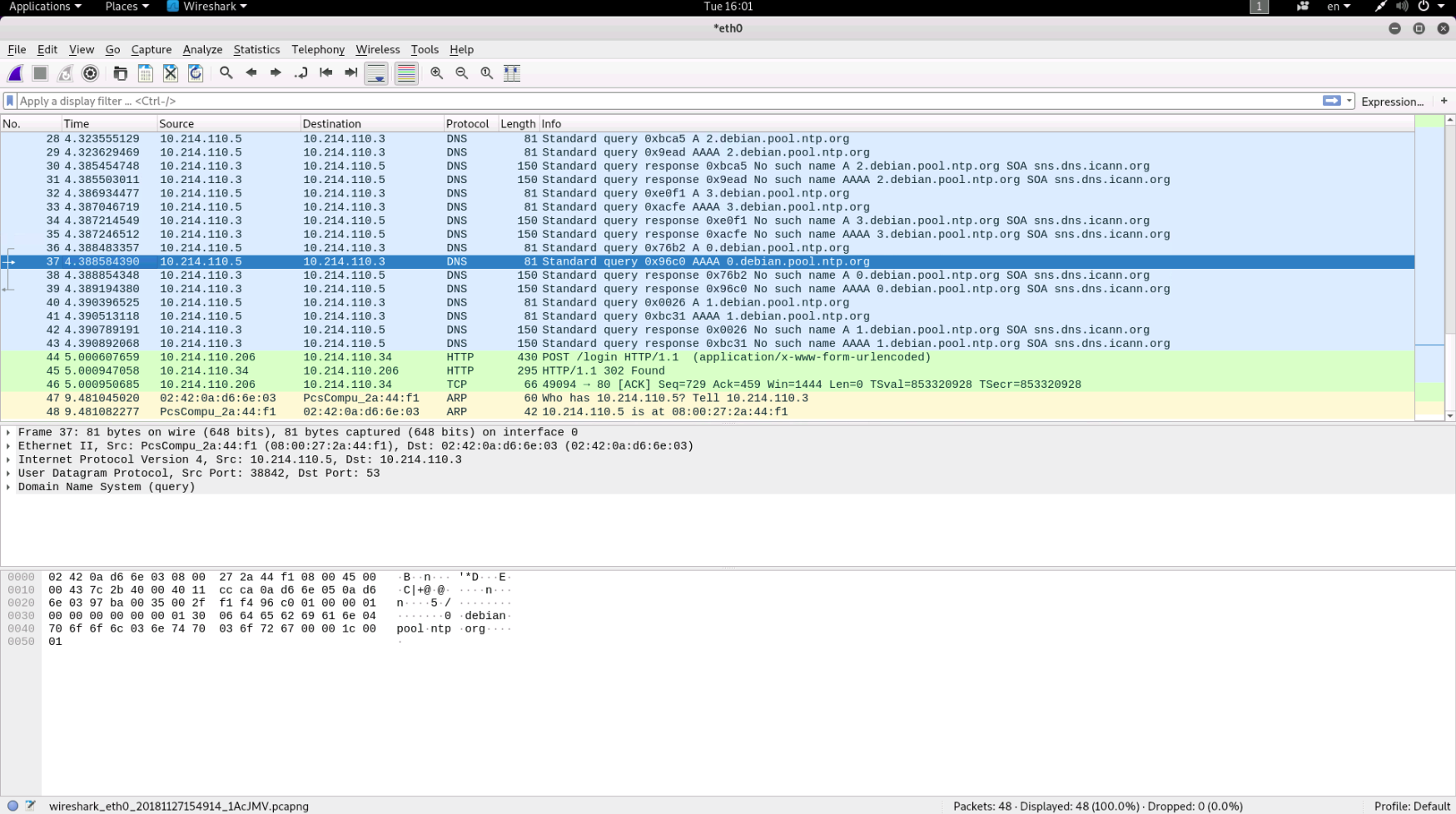
As you will notice the box in the middle keep updating. This is a list off all the packets send and received in the network, where each row represents a packet. The row is split into seven columns, showing some information about each packet, this information is things like destination, source and protocol. The packets is coloured coded based on which protocol they are send with.
The contents of the packets can be examined in the field just bellow. Here you will find more information about each protocol used in the transmission. Try examining this and see if you find anything that might be interesting.
HINT 1: Start by looking at the HTTP packets.